synology??Jack12345 写了: 2024年 11月 20日 19:39 我很久以前 是个音响低烧友。然后在中国淘宝上 买了 2个 3T的硬盘,拷满了 96KHz, 24Bits 的无损压缩的 高清音乐
然后 在这边 也给同事们分享,特别是几个香港发烧友同事,也算 做了个人情吧
为了 在家里 也大家一起分享,我买了个 Qnap 的 NAS 系统。然后 把音乐硬盘 插上去了。结果 大事不妙,灯拼命闪,赶紧拔电源,把硬盘拿出来,发现已经被 全盘格式化 format 了。3T的音乐 荡然无存。血泪教训
像这种软件,全盘格式化 都不问一声的,这几十年来 我是第一次见到。真是 有多远 离多远
其实 这种家庭分享的,买个硬盘盒,装个硬盘,往路由器上的 USB 接口上 一插 不就完事了?浪费 那个冤枉钱 ?
千万不要买 Qnap 等 NAS 系统
版主: Jack12345
-
cellcycle1
- 论坛元老

cellcycle1 的博客 - 帖子互动: 1051
- 帖子: 71124
- 注册时间: 2022年 7月 24日 15:59
#21 Re: 千万不要买 Qnap 等 NAS 系统
#22 Re: 千万不要买 Qnap 等 NAS 系统
下一站Unraid!
helloguys 写了: 2024年 11月 21日 17:32 没有嘲笑的意思,但顶楼这种帖子,跟拿杀虫剂对付千年虫一样。稍有常识都知道,把一个移动硬盘插到 NAS 的 USB 口,缺省的操作不会是格式化硬盘。再脑残的产品经理也不会这样设计。说实在的,我用 QNAP 也小20年了,要达到顶楼这种效果,还真没琢磨出来该怎样设置。
我的 NAS 历程是: PC -> QNAP -> Synology -> 黑群晖 -> 在 QNAP 上安装黑群晖。至于为什么要在 QNAP 上安装黑群晖,可以写一本书。但20年的经验告诉我,这是优解(耗电、噪音、体积、散热、功能、可玩性)。
-
cellcycle1
- 论坛元老

cellcycle1 的博客 - 帖子互动: 1051
- 帖子: 71124
- 注册时间: 2022年 7月 24日 15:59
-
wolfstar76(Wolfstar)
- 著名写手

- 帖子互动: 16
- 帖子: 242
- 注册时间: 2022年 9月 11日 16:12
#26 Re: 千万不要买 Qnap 等 NAS 系统
那时候的 无损压缩格式 好像是 APE 吧,不知道现在流行什么压缩格式了,FLAC ?
然后 你用 APE 做为关键词 在淘宝搜索一下,可以找到几个卖家。联系他们,他们 会给你寄个 excel 文件,有各种音乐,交响乐 流行歌曲 欧美流行 影视音乐 动画音乐 游戏音乐等,各种门类的都有。然后 你就从他们那边买 空白硬盘,市场价。然后 你选好音乐后,他们帮你拷满 硬盘。
比如 硬盘 1000 人民币一个,再加 200元 拷贝人工费用。然后 装满了音乐 就给你寄过来了。好像只寄国内的吧,国际的 不知道 邮寄不 ??
我是 10年前买的。不知道现在是否还有这项服务了?算属于侵犯版权的
主流格式是 96KHz 24bits的,所谓的音乐母带,不知道 他们从哪边找来的。一般这样的 也够了。还有更高的 192KHz 的,那个好像没必要。
2声道的 96KHz 24bits 我感觉 已经足够好了,瓶颈在音箱上,不在音源上了。如果 想要更好的 听觉效果,那就要多声道了,2声道的 到头了
上次由 Jack12345 在 2024年 11月 21日 22:27 修改。
原因: 未提供修改原因
原因: 未提供修改原因
-
wolfstar76(Wolfstar)
- 著名写手

- 帖子互动: 16
- 帖子: 242
- 注册时间: 2022年 9月 11日 16:12
#27 Re: 千万不要买 Qnap 等 NAS 系统
謝謝,我回國再去查,現在淘寶都無法登錄,沒有國内手機號碼。Jack12345 写了: 2024年 11月 21日 22:26 那时候的 无损压缩格式 好像是 APE 吧,不知道现在流行什么压缩格式了,FLAC ?
然后 你用 APE 做为关键词 在淘宝搜索一下,可以找到几个卖家。联系他们,他们 会给你寄个 excel 文件,有各种音乐,交响乐 流行歌曲 欧美流行 影视音乐 动画音乐 游戏音乐等,各种门类的都有。然后 你就从他们那边买 空白硬盘,市场价。然后 你选好音乐后,他们帮你拷满 硬盘。
比如 硬盘 1000 人民币一个,再加 200元 拷贝人工费用。然后 装满了音乐 就给你寄过来了。好像只寄国内的吧,国际的 不知道 邮寄不 ??
我是 10年前买的。不知道现在是否还有这项服务了?算属于侵犯版权的
主流格式是 96KHz 24bits的,所谓的音乐母带,不知道 他们从哪边找来的。一般这样的 也够了。还有更高的 192KHz 的,那个好像没必要。
2声道的 96KHz 24bits 我感觉 已经足够好了,瓶颈在音箱上,不在音源上了。如果 想要更好的 听觉效果,那就要多声道了,2声道的 到头了
#28 Re: 千万不要买 Qnap 等 NAS 系统
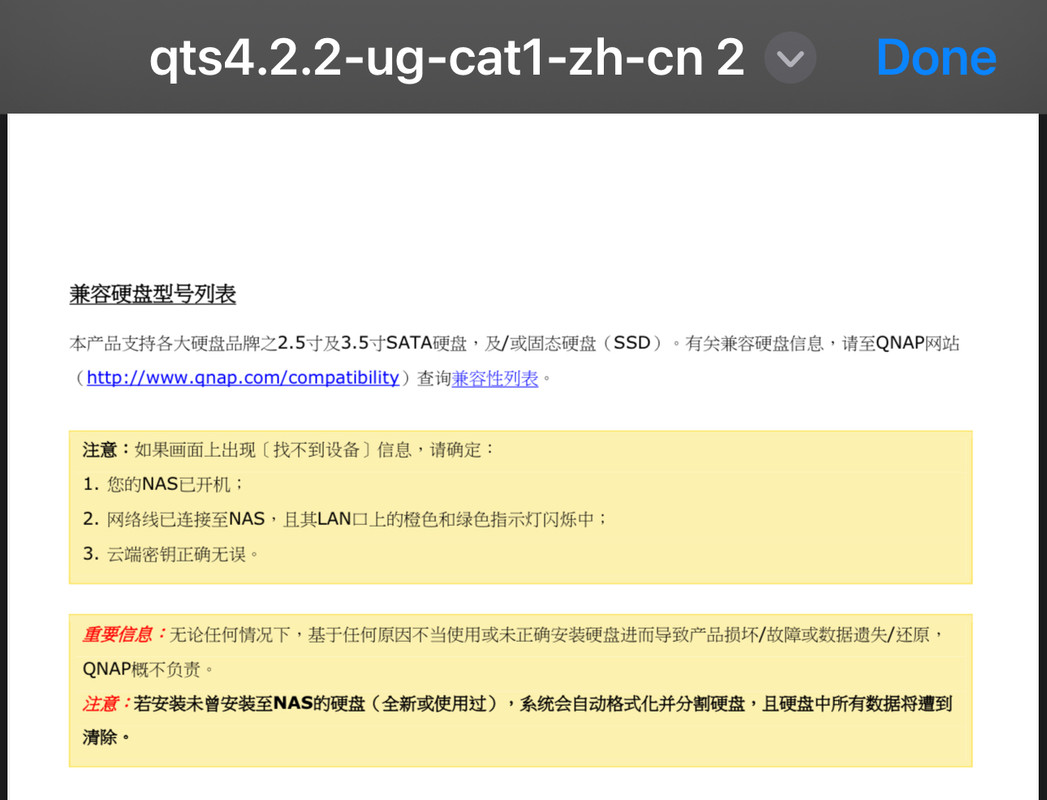
谢谢 找出手册来。果然会格式化吧
前面还有个 ID 还非要辩护 【稍有常识都知道,把一个移动硬盘插到 NAS 的 USB 口,缺省的操作不会是格式化硬盘。再脑残的产品经理也不会这样设计。】
打脸了吧,就是 这么脑残的设计。前面还有人 reset 一下,几个硬盘的东西 全没了,不是一般的脑残设计。这么危险的东西 就跟定时炸弹一样
这种警告 都要 红体大字 印在手册的封面上 警告。而不是在 说明书的某一页的底下。这就像 你的汽车设计 和大家的相反的,油门在左边 刹车在右边,然后不是【我的说明书里都说了啊 】这么简单一句话 就可以推卸责任的
现在家里 内网用用 就在路由器上插个硬盘就可以了。外网分享 不是 各种 cloud 多如牛毛?NAS 这种老早该淘汰了,就像 电灯 淘汰 煤油灯一样
#30 Re: 千万不要买 Qnap 等 NAS 系统
Syno, unraid都是在设置web ui 上有警告,这货自动清零么?如果这样太S B了。
Jack12345 写了: 2024年 11月 22日 18:50 谢谢 找出手册来。果然会格式化吧
前面还有个 ID 还非要辩护 【稍有常识都知道,把一个移动硬盘插到 NAS 的 USB 口,缺省的操作不会是格式化硬盘。再脑残的产品经理也不会这样设计。】
打脸了吧,就是 这么脑残的设计。前面还有人 reset 一下,几个硬盘的东西 全没了,不是一般的脑残设计。这么危险的东西 就跟定时炸弹一样
这种警告 都要 红体大字 印在手册的封面上 警告。而不是在 说明书的某一页的底下。这就像 你的汽车设计 和大家的相反的,油门在左边 刹车在右边,然后不是【我的说明书里都说了啊 】这么简单一句话 就可以推卸责任的
现在家里 内网用用 就在路由器上插个硬盘就可以了。外网分享 不是 各种 cloud 多如牛毛?NAS 这种老早该淘汰了,就像 电灯 淘汰 煤油灯一样
#33 Re: 千万不要买 Qnap 等 NAS 系统
QNAP Security Advisory
Bulletin ID: QSA-24-36, QSA-24-37, QSA-24-39, QSA-24-40, QSA-24-43, QSA-24-44, QSA-24-46, QSA-24-47
QVPN beta
Taipei, Taiwan, November 23, 2024 - QNAP® had published security enhancement against security vulnerabilities that could affect specific versions of QNAP products. Please use the following information and solutions to correct the security issues and vulnerabilities.
This advisory includes the following:
Multiple Vulnerabilities in Notes Station 3 (ID: QSA-24-36)
Multiple Vulnerabilities in OpenSSH (ID: QSA-24-37)
Multiple Vulnerabilities in Photo Station (ID: QSA-24-39)
Vulnerability in QNAP AI Core (ID: QSA-24-40)
Multiple Vulnerabilities in QTS and QuTS hero (ID: QSA-24-43)
Multiple Vulnerabilities in QuRouter (ID: QSA-24-44)
Vulnerability in QuLog Center (ID: QSA-24-46)
Vulnerability in Media Streaming Add-on (ID: QSA-24-47)
Multiple Vulnerabilities in Notes Station 3
Security ID: QSA-24-36
Release date: November 23, 2024
CVE identifier: CVE-2024-38643 | CVE-2024-38644 | CVE-2024-38645 | CVE-2024-38646
Severity: Important
Status: Resolved
Affected products: Notes Station 3 version 3.9.x
Summary
Multiple vulnerabilities have been reported to affect Notes Station 3:
CVE-2024-38643: If exploited, the missing authentication for critical function vulnerability could allow remote attackers to gain access to the system.
CVE-2024-38644: If exploited, the command injection vulnerability could allow remote attackers who have gained user access to execute arbitrary commands.
CVE-2024-38645: If exploited, the server-side request forgery (SSRF) vulnerability could allow remote attackers who have gained user access to read application data.
CVE-2024-38646: If exploited, the incorrect permission assignment for critical resource vulnerability could allow local attackers who have gained administrator access to gain unauthorized access to data.
We have already fixed the vulnerabilities in the following version:
Affected Product Fixed Version
Notes Station 3 version 3.9.x Notes Station 3 version 3.9.7 and later
<<Learn more>>
Multiple Vulnerabilities in OpenSSH
Security ID: QSA-24-37
Release date: November 23, 2024
CVE identifier: CVE-2023-38408 | CVE-2021-41617 | CVE-2020-14145
Severity: Moderate
Status: Resolved
Affected products: QTS 5.1.x, QuTS hero h5.1.x
Summary
Multiple vulnerabilities have been reported in OpenSSH. The vulnerabilities have been found to affect certain QNAP operating system versions.
We have already fixed the vulnerabilities in the following versions:
Affected Product Fixed Version
QTS 5.1.x QTS 5.1.8.2823 build 20240712 and later
QuTS hero h5.1.x QuTS hero h5.1.8.2823 build 20240712 and later
<<Learn more>>
Multiple Vulnerabilities in Photo Station
Security ID: QSA-24-39
Release date: November 23, 2024
CVE identifier: CVE-2024-32767 | CVE-2024-32768 | CVE-2024-32769 | CVE-2024-32770
Severity: Moderate
Status: Resolved
Affected products: Photo Station 6.4.x
Summary
Multiple vulnerabilities have been reported to affect Photo Station:
CVE-2024-32767, CVE-2024-32768, CVE-2024-32769, CVE-2024-32770: If exploited, the cross-site scripting (XSS) vulnerabilities could allow remote attackers who have gained user access to bypass security mechanisms or read application data.
We have already fixed the vulnerabilities in the following version:
Affected Product Fixed Version
Photo Station 6.4.x Photo Station 6.4.3 (2024/07/12) and later
<<Learn more>>
Vulnerability in QNAP AI Core
Security ID: QSA-24-40
Release date: November 23, 2024
CVE identifier: CVE-2024-38647
Severity: Important
Status: Resolved
Affected products: QNAP AI Core 3.4.x
Summary
An exposure of sensitive information vulnerability has been reported to affect QNAP AI Core. If exploited, the vulnerability could allow remote attackers to compromise the security of the system.
We have already fixed the vulnerability in the following version:
Affected Product Fixed Version
QNAP AI Core 3.4.x QNAP AI Core 3.4.1 and later
<<Learn more>>
Multiple Vulnerabilities in QTS and QuTS hero
Security ID: QSA-24-43
Release date: November 23, 2024
CVE identifier: CVE-2024-37041 | CVE-2024-37042 | CVE-2024-37043 | CVE-2024-37044 | CVE-2024-37045 | CVE-2024-37046 | CVE-2024-37047 | CVE-2024-37048 | CVE-2024-37049 | CVE-2024-37050 | CVE-2024-50396 | CVE-2024-50397 | CVE-2024-50398 | CVE-2024-50399 | CVE-2024-50400
Severity: Important
Status: Resolved
Affected products: QTS 5.2.x, QuTS hero h5.2.x
Summary
Multiple vulnerabilities have been reported to affect certain QNAP operating system versions:
CVE-2024-37041, CVE-2024-37044, CVE-2024-37047, CVE-2024-37049, CVE-2024-37050: If exploited, the buffer overflow vulnerabilities could allow remote attackers who have gained administrator access to modify memory or crash processes.
CVE-2024-37042, CVE-2024-37045, CVE-2024-37048: If exploited, the NULL pointer dereference vulnerabilities could allow remote attackers who have gained administrator access to launch a denial-of-service (DoS) attack.
CVE-2024-37043, CVE-2024-37046: If exploited, the path traversal vulnerabilities could allow remote attackers who have gained administrator access to read the contents of unexpected files or system data.
CVE-2024-50396, CVE-2024-50397, CVE-2024-50398, CVE-2024-50399, CVE-2024-50400, CVE-2024-50401: If exploited, the use of externally-controlled format string vulnerabilities could allow remote attackers to obtain secret data or modify memory.
We have already fixed the vulnerabilities in the following versions:
Affected Product Fixed Version
QTS 5.2.x QTS 5.2.1.2930 build 20241025 and later
QuTS hero h5.2.x QuTS hero h5.2.1.2929 build 20241025 and later
<<Learn more>>
Multiple Vulnerabilities in QuRouter
Security ID: QSA-24-44
Release date: November 23, 2024
CVE identifier: CVE-2024-48860 | CVE-2024-48861
Severity: Important
Status: Resolved
Affected products: QuRouter 2.4.x
Summary
Multiple vulnerabilities have been reported to affect QuRouter:
CVE-2024-48860, CVE-2024-48861: If exploited, the command injection vulnerabilities could allow remote attackers to execute arbitrary commands.
We have already fixed the vulnerabilities in the following version:
Affected Product Fixed Version
QuRouter 2.4.x QuRouter 2.4.3.106 and later
<<Learn more>>
Vulnerability in QuLog Center
Security ID: QSA-24-46
Release date: November 23, 2024
CVE identifier: CVE-2024-48862
Severity: Important
Status: Resolved
Affected products: QuLog Center 1.7.x and 1.8.x
Summary
A link following vulnerability has been reported to affect QuLog Center. If exploited, the vulnerability could allow remote attackers to traverse the file system to unintended locations.
We have already fixed the vulnerability in the following versions:
Affected Product Fixed Version
QuLog Center 1.7.x QuLog Center 1.7.0.831 (2024/10/15) and later
QuLog Center 1.8.x QuLog Center 1.8.0.888 (2024/10/15) and later
<<Learn more>>
Vulnerability in Media Streaming Add-on
Security ID: QSA-24-47
Release date: November 23, 2024
CVE identifier: CVE-2024-50395
Severity: Moderate
Status: Resolved
Affected products: Media Streaming Add-on 500.1.x
Summary
An authorization bypass through user-controlled key vulnerability has been reported to affect Media Streaming add-on. If exploited, the vulnerability could allow attackers with local network access to gain unintended privileges.
We have already fixed the vulnerability in the following version:
Affected Product Fixed Version
Media Streaming Add-on 500.1.x Media Streaming Add-on 500.1.1.6 (2024/08/02) and later
<<Learn more>>
If you have any questions regarding this issue, please contact us at https://www.qnap.com/go/support-ticket/.
Bulletin ID: QSA-24-36, QSA-24-37, QSA-24-39, QSA-24-40, QSA-24-43, QSA-24-44, QSA-24-46, QSA-24-47
QVPN beta
Taipei, Taiwan, November 23, 2024 - QNAP® had published security enhancement against security vulnerabilities that could affect specific versions of QNAP products. Please use the following information and solutions to correct the security issues and vulnerabilities.
This advisory includes the following:
Multiple Vulnerabilities in Notes Station 3 (ID: QSA-24-36)
Multiple Vulnerabilities in OpenSSH (ID: QSA-24-37)
Multiple Vulnerabilities in Photo Station (ID: QSA-24-39)
Vulnerability in QNAP AI Core (ID: QSA-24-40)
Multiple Vulnerabilities in QTS and QuTS hero (ID: QSA-24-43)
Multiple Vulnerabilities in QuRouter (ID: QSA-24-44)
Vulnerability in QuLog Center (ID: QSA-24-46)
Vulnerability in Media Streaming Add-on (ID: QSA-24-47)
Multiple Vulnerabilities in Notes Station 3
Security ID: QSA-24-36
Release date: November 23, 2024
CVE identifier: CVE-2024-38643 | CVE-2024-38644 | CVE-2024-38645 | CVE-2024-38646
Severity: Important
Status: Resolved
Affected products: Notes Station 3 version 3.9.x
Summary
Multiple vulnerabilities have been reported to affect Notes Station 3:
CVE-2024-38643: If exploited, the missing authentication for critical function vulnerability could allow remote attackers to gain access to the system.
CVE-2024-38644: If exploited, the command injection vulnerability could allow remote attackers who have gained user access to execute arbitrary commands.
CVE-2024-38645: If exploited, the server-side request forgery (SSRF) vulnerability could allow remote attackers who have gained user access to read application data.
CVE-2024-38646: If exploited, the incorrect permission assignment for critical resource vulnerability could allow local attackers who have gained administrator access to gain unauthorized access to data.
We have already fixed the vulnerabilities in the following version:
Affected Product Fixed Version
Notes Station 3 version 3.9.x Notes Station 3 version 3.9.7 and later
<<Learn more>>
Multiple Vulnerabilities in OpenSSH
Security ID: QSA-24-37
Release date: November 23, 2024
CVE identifier: CVE-2023-38408 | CVE-2021-41617 | CVE-2020-14145
Severity: Moderate
Status: Resolved
Affected products: QTS 5.1.x, QuTS hero h5.1.x
Summary
Multiple vulnerabilities have been reported in OpenSSH. The vulnerabilities have been found to affect certain QNAP operating system versions.
We have already fixed the vulnerabilities in the following versions:
Affected Product Fixed Version
QTS 5.1.x QTS 5.1.8.2823 build 20240712 and later
QuTS hero h5.1.x QuTS hero h5.1.8.2823 build 20240712 and later
<<Learn more>>
Multiple Vulnerabilities in Photo Station
Security ID: QSA-24-39
Release date: November 23, 2024
CVE identifier: CVE-2024-32767 | CVE-2024-32768 | CVE-2024-32769 | CVE-2024-32770
Severity: Moderate
Status: Resolved
Affected products: Photo Station 6.4.x
Summary
Multiple vulnerabilities have been reported to affect Photo Station:
CVE-2024-32767, CVE-2024-32768, CVE-2024-32769, CVE-2024-32770: If exploited, the cross-site scripting (XSS) vulnerabilities could allow remote attackers who have gained user access to bypass security mechanisms or read application data.
We have already fixed the vulnerabilities in the following version:
Affected Product Fixed Version
Photo Station 6.4.x Photo Station 6.4.3 (2024/07/12) and later
<<Learn more>>
Vulnerability in QNAP AI Core
Security ID: QSA-24-40
Release date: November 23, 2024
CVE identifier: CVE-2024-38647
Severity: Important
Status: Resolved
Affected products: QNAP AI Core 3.4.x
Summary
An exposure of sensitive information vulnerability has been reported to affect QNAP AI Core. If exploited, the vulnerability could allow remote attackers to compromise the security of the system.
We have already fixed the vulnerability in the following version:
Affected Product Fixed Version
QNAP AI Core 3.4.x QNAP AI Core 3.4.1 and later
<<Learn more>>
Multiple Vulnerabilities in QTS and QuTS hero
Security ID: QSA-24-43
Release date: November 23, 2024
CVE identifier: CVE-2024-37041 | CVE-2024-37042 | CVE-2024-37043 | CVE-2024-37044 | CVE-2024-37045 | CVE-2024-37046 | CVE-2024-37047 | CVE-2024-37048 | CVE-2024-37049 | CVE-2024-37050 | CVE-2024-50396 | CVE-2024-50397 | CVE-2024-50398 | CVE-2024-50399 | CVE-2024-50400
Severity: Important
Status: Resolved
Affected products: QTS 5.2.x, QuTS hero h5.2.x
Summary
Multiple vulnerabilities have been reported to affect certain QNAP operating system versions:
CVE-2024-37041, CVE-2024-37044, CVE-2024-37047, CVE-2024-37049, CVE-2024-37050: If exploited, the buffer overflow vulnerabilities could allow remote attackers who have gained administrator access to modify memory or crash processes.
CVE-2024-37042, CVE-2024-37045, CVE-2024-37048: If exploited, the NULL pointer dereference vulnerabilities could allow remote attackers who have gained administrator access to launch a denial-of-service (DoS) attack.
CVE-2024-37043, CVE-2024-37046: If exploited, the path traversal vulnerabilities could allow remote attackers who have gained administrator access to read the contents of unexpected files or system data.
CVE-2024-50396, CVE-2024-50397, CVE-2024-50398, CVE-2024-50399, CVE-2024-50400, CVE-2024-50401: If exploited, the use of externally-controlled format string vulnerabilities could allow remote attackers to obtain secret data or modify memory.
We have already fixed the vulnerabilities in the following versions:
Affected Product Fixed Version
QTS 5.2.x QTS 5.2.1.2930 build 20241025 and later
QuTS hero h5.2.x QuTS hero h5.2.1.2929 build 20241025 and later
<<Learn more>>
Multiple Vulnerabilities in QuRouter
Security ID: QSA-24-44
Release date: November 23, 2024
CVE identifier: CVE-2024-48860 | CVE-2024-48861
Severity: Important
Status: Resolved
Affected products: QuRouter 2.4.x
Summary
Multiple vulnerabilities have been reported to affect QuRouter:
CVE-2024-48860, CVE-2024-48861: If exploited, the command injection vulnerabilities could allow remote attackers to execute arbitrary commands.
We have already fixed the vulnerabilities in the following version:
Affected Product Fixed Version
QuRouter 2.4.x QuRouter 2.4.3.106 and later
<<Learn more>>
Vulnerability in QuLog Center
Security ID: QSA-24-46
Release date: November 23, 2024
CVE identifier: CVE-2024-48862
Severity: Important
Status: Resolved
Affected products: QuLog Center 1.7.x and 1.8.x
Summary
A link following vulnerability has been reported to affect QuLog Center. If exploited, the vulnerability could allow remote attackers to traverse the file system to unintended locations.
We have already fixed the vulnerability in the following versions:
Affected Product Fixed Version
QuLog Center 1.7.x QuLog Center 1.7.0.831 (2024/10/15) and later
QuLog Center 1.8.x QuLog Center 1.8.0.888 (2024/10/15) and later
<<Learn more>>
Vulnerability in Media Streaming Add-on
Security ID: QSA-24-47
Release date: November 23, 2024
CVE identifier: CVE-2024-50395
Severity: Moderate
Status: Resolved
Affected products: Media Streaming Add-on 500.1.x
Summary
An authorization bypass through user-controlled key vulnerability has been reported to affect Media Streaming add-on. If exploited, the vulnerability could allow attackers with local network access to gain unintended privileges.
We have already fixed the vulnerability in the following version:
Affected Product Fixed Version
Media Streaming Add-on 500.1.x Media Streaming Add-on 500.1.1.6 (2024/08/02) and later
<<Learn more>>
If you have any questions regarding this issue, please contact us at https://www.qnap.com/go/support-ticket/.
草你特铐谱祖宗十八代加后十八代 你踏马的去死吧
#36 Re: 千万不要买 Qnap 等 NAS 系统
辩护的那个是说移动硬盘插到NAS的USB口上Jack12345 写了: 2024年 11月 22日 18:50 谢谢 找出手册来。果然会格式化吧
前面还有个 ID 还非要辩护 【稍有常识都知道,把一个移动硬盘插到 NAS 的 USB 口,缺省的操作不会是格式化硬盘。再脑残的产品经理也不会这样设计。】
打脸了吧,就是 这么脑残的设计。前面还有人 reset 一下,几个硬盘的东西 全没了,不是一般的脑残设计。这么危险的东西 就跟定时炸弹一样
这种警告 都要 红体大字 印在手册的封面上 警告。而不是在 说明书的某一页的底下。这就像 你的汽车设计 和大家的相反的,油门在左边 刹车在右边,然后不是【我的说明书里都说了啊 】这么简单一句话 就可以推卸责任的
现在家里 内网用用 就在路由器上插个硬盘就可以了。外网分享 不是 各种 cloud 多如牛毛?NAS 这种老早该淘汰了,就像 电灯 淘汰 煤油灯一样
顶楼的是把两个裸硬盘直接装入NAS内了吧?这样NAS电路板上电唤醒后,就认为自己是在生产线上,刚刚被装入两块硬盘,所以进行格式化,做好出厂准备?